搜索结果: 1-15 共查到“Reduced”相关记录447条 . 查询时间(0.296 秒)
Layer-by-layer assembly of nanomultilayer structures: Reinforcement of expanded char reduced the toxicity and fire hazard of epoxy resins
Epoxy resin Fire safety Intumescent flame retardant Smoke suppression Flame retardancy
2023/11/16
Epoxy resins (EP) have been widely applied in chemical engineering, composite materials, and aerospace. Nevertheless, the high fire hazard of flammable epoxy resins, which release considerable hazardo...
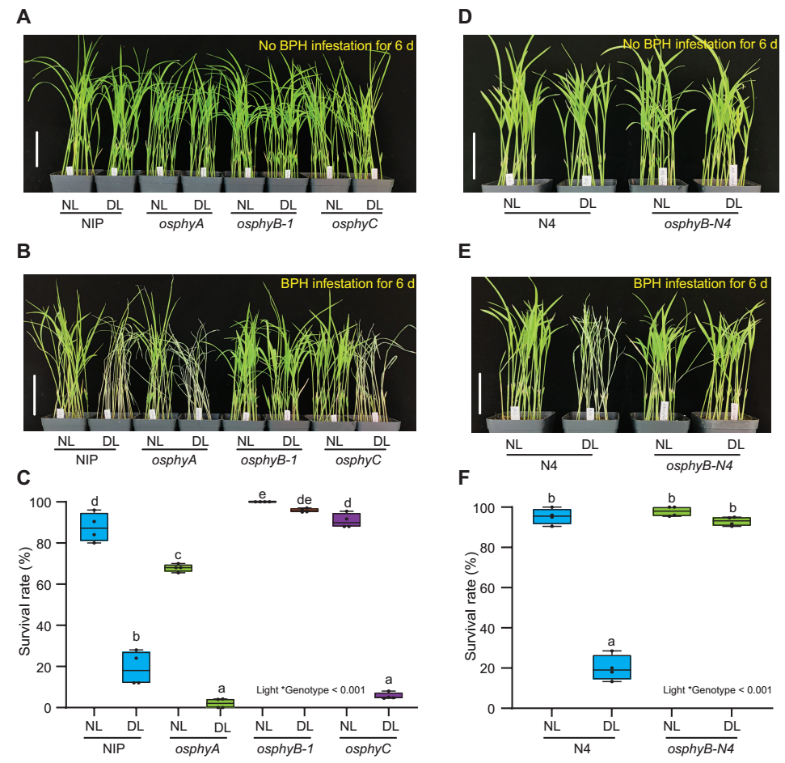
南京农业大学农学院《Plant Physiology》发表万建民院士团队“Phytochrome B mediates dim-light-reduced insect resistance by promoting the ethylene pathway in rice”(图)
万建民 水稻褐飞虱 基因
2023/10/28
褐飞虱是水稻生产中最严重的害虫。褐飞虱通过针状口器刺入水稻叶鞘组织吸食韧皮部汁液,造成水稻严重减产甚至绝收。种植抗性品种是综合防控褐飞虱的基础。然而植物抗病虫性通常受光照、温度和湿度等环境因素的影响,在一定程度上制约了抗性基因的有效利用。如采用密植的栽培方式是当前许多作物增加单位面积产量的重要途径,但是密植通常会导致冠层以下的植株部分光照不足而产生庇荫反应,易滋生各类病虫害,虽然这种现象普遍存在,...
Cryptanalysis of Round-Reduced KECCAK using Non-Linear Structures
KECCAK SHA-3 Hash function
2019/8/2
In this paper, we present new preimage attacks on KECCAK-384 and KECCAK-512 for 2, 3 and 4 rounds. The attacks are based on non-linear structures (structures that contain quadratic terms). These struc...
SipHash is a family of ARX-based MAC algorithms optimized for short inputs. Already, a lot of implementations and applications for SipHash have been proposed, whereas the cryptanalysis of SipHash stil...
In this paper we investigate the security of 5-round AES against two different attacks in an adaptive setting. We present a practical key-recovery attack on 5-round AES with a secret s-box that requir...
Mixture Integral Attacks on Reduced-Round AES with a Known/Secret S-Box
AES Mixture Differential Cryptanalysis Secret-Key Distinguisher
2019/7/8
The starting point of our work is “Mixture Differential Cryptanalysis” recently introduced at FSE/ToSC 2019, a way to turn the “multiple-of-8” 5-round AES secret-key distinguisher presented at Eurocry...

Study ties poor sleep to reduced memory performance in older adults(图)
poor sleep reduced memory performance older adults
2019/10/23
A new study has found that variability in night-to-night sleep time and reduced sleep quality adversely affect the ability of older adults to recall information about past events.Although further inve...
New Semi-Free-Start Collision Attack Framework for Reduced RIPEMD-160
hash function RIPEMD-160 freedom degree utilization
2019/6/10
RIPEMD-160 is a hash function published in 1996, which shares similarities with other hash functions designed in this time-period like MD4, MD5 and SHA-1. However, for RIPEMD-160, no (semi-free-start)...
Preimage Attacks on Reduced Troika with Divide-and-Conquer Methods
hash function Troika preimage
2019/6/4
Troika is a recently proposed sponge-based hash function for IOTA's ternary architecture and platform, which is developed by CYBERCRYPT. In this paper, we introduce the preimage attack on 2 and 3 roun...
Distinguishers on round-reduced AES have attracted considerable attention in the recent years. Although the number of rounds covered in key-recovery attacks has not been increased since, subspace, yoy...
The Mersenne Low Hamming Combination Search Problem can be reduced to an ILP Problem
Post-Quantum Cryptography Cryptanalysis Public-Key Cryptography Integer Linear Programming
2019/5/13
In 2017, Aggarwal, Joux, Prakash, and Santha proposed an innovative NTRU-like public-key cryptosystem that was believed to be quantum resistant, based on Mersenne prime numbers q=2N−1q=2N−...
Practical Key-recovery Attacks on Round-Reduced Ketje Jr, Xoodoo-AE and Xoodyak
Conditional Cube Attack Keccak Ketje Jr
2019/5/9
Conditional cube attack was proposed by Huang et al. at EUROCRYPT 2017 to attack Keccak keyed mode. Inspired by dynamic cube attack, they reduce the degree by appending key bit conditions on the initi...
Miller Inversion is Easy for the Reduced Tate Pairing on Trace Zero Supersingular Curves
elliptic curve cryptosystem pairing inversion Tate pairing
2019/4/16
We present a simple algorithm for Miller inversion for the reduced Tate pairing on supersingular elliptic curve of trace zero defined over the finite fields with q elements. Our algorithm runs with O(...
Key-dependent cube attack on reduced Frit permutation in Duplex-AE modes
Frit Duplex authenticated encryption mode Key-dependent cube attack
2019/2/25
Frit is a new lightweight 384-bit cryptographic permutation proposed by Simon et al., which is designed for resisting fault injection and performs competitively in both hardware and software. Dobrauni...
Continuous Key Agreement with Reduced Bandwidth
Double Ratchet Protocol Continuous Key Agreement Post Quantum Cryptography
2019/1/29
Continuous Key Agreement (CKA) is a two-party procedure used by Double Ratchet protocols (e. g., Signal). This is a continuous and synchronous protocol that generates a fresh key for every sent/receiv...

